Troubleshoot Ticket
Network Team uses telnet (port 23) to login in the device 10.1.1.1
Need to restrict the use of telnet since telnet is not secure ; session is not encrypted
Enable ssh (port 22) which is secure protocol and where the session is encrypted
Can be configured in working hours since no downtime is required
========================================================
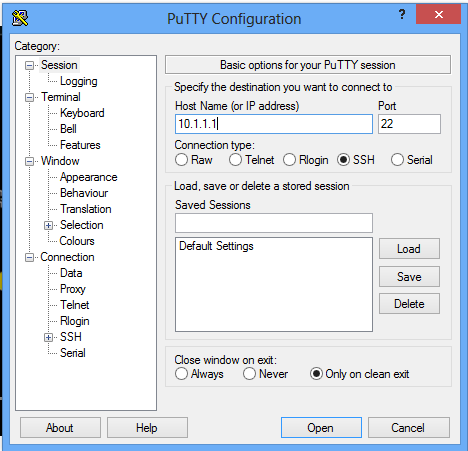
Lets open Putty and try to login via ssh to device 10.1.1.1
Here we can see we are getting error - Connection refused which means ssh is not enabled on the device
10.1.1.1 and to solve it we need to enable ssh
Now lets try to login via telnet
We are able to login via telnet !
So lets enable SSH
Telnet session is insecure because the information is in the clear text
For SSH session that is not the case , for ssh session the information is encrypted .
To encrypt / decrypt any information or data we need to generate certain keys which are associated with the hostname and domain name .
So lets first configure a hostname and domain name for the device
R1(config)#hostname PUNE_ROUTER
PUNE_ROUTER(config)#
PUNE_ROUTER(config)#ip domain name amartechstuff.net
PUNE_ROUTER(config)#
Note:- I am just configuring a random domain name . If you are working in real environment your
organization will have valid public domain name .
Now lets move forward and generate crypto keys which will be used to encrypt / decrypt the information
PUNE_ROUTER(config)#crypto key generate rsa
The name for the keys will be: PUNE_ROUTER.amartechstuff.net
Choose the size of the key modulus in the range of 360 to 4096 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take
a few minutes.
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys, keys will be non-exportable...
[OK] (elapsed time was 1 seconds)
PUNE_ROUTER(config)#
*Aug 8 12:16:18.659: %SSH-5-ENABLED: SSH 1.99 has been enabled
PUNE_ROUTER(config)#^Z
You can see that the name of the key is PUNE_ROUTER.amartechstuff.net i.e
hostname + domain name
Lets see the key
PUNE_ROUTER#sh ip ssh
SSH Enabled - version 1.99
Authentication timeout: 120 secs; Authentication retries: 3
Minimum expected Diffie Hellman key size : 1024 bits
IOS Keys in SECSH format(ssh-rsa, base64 encoded):
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAAAgQDfHDOhreEAVbaifqV56LS1qTGicGEC+2s0EqRwA4Ef
qIh8DS029RxkaLYll4iKlxkdJ6Qu/TphdbefEmpSidzVu+gJ80NUUxmlpiMGtF0SY5Yzd6VCsvyRFQo8
dwsdioq686NK+UpYGh46mM3GxP2cDKuvT7ytdDlBSgnsWKn04w==
PUNE_ROUTER#
Now the next and last step is to check and enable ssh under line vty
line vty 0 4
login local
transport input telnet
line vty 5 15
login local
transport input telnet
Now we can see that telnet is configured .
Lets change it to ssh
PUNE_ROUTER#config
Configuring from terminal, memory, or network [terminal]?
Enter configuration commands, one per line. End with CNTL/Z.
PUNE_ROUTER(config)#line vty 0 15
PUNE_ROUTER(config-line)#transport input ssh
PUNE_ROUTER(config-line)#^Z
Now lets check whether ssh is enabled or not
https://networkengineerstuff.blogspot.com