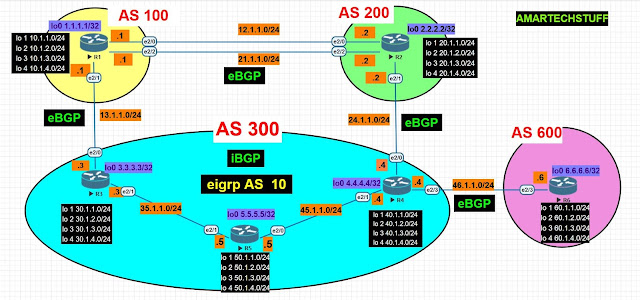
Task:- Understanding BGP Synchronization Rule
Dont use or advertise the routes to eBGP learned by iBGP neighbor unless and until
same are learned via other IGP .
By default BGP Synchronization Rule is not enabled.
R3 have eBGP neighbor as R1 and iBGP neighbor as R4
!!On R4 lets create an loopback and advertise to R3 via iBGP
and then check on R3 and R4 what is happening !!
Remember one thing we wont advertise the same network via any IGP
R4(config)#int loopback 400
R4(config-if)#ip address 140.0.0.1 255.255.255.0
R4(config)#router bgp 300
R4(config-router)#network 140.0.0.0 mask 255.255.255.0
R4#sh ip bgp 140.0.0.0
BGP routing table entry for 140.0.0.0/24, version 39
Paths: (1 available, best #1, table default)
Advertised to update-groups:
2 4
Refresh Epoch 1
Local
0.0.0.0 from 0.0.0.0 (40.1.4.1)
Origin IGP, metric 0, localpref 100, weight 32768, valid, sourced, local, best
rx pathid: 0, tx pathid: 0x0
Lets check on R3
R3#sh ip bgp 140.0.0.0
BGP routing table entry for 140.0.0.0/24, version 39
Paths: (1 available, best #1, table default)
Advertised to update-groups:
3
Refresh Epoch 1
Local
4.4.4.4 (metric 435200) from 4.4.4.4 (40.1.4.1)
Origin IGP, metric 0, localpref 100, valid, internal, best
rx pathid: 0, tx pathid: 0x0
The route is present in Bgp table of R3
But lets check whether it is using it or not
For that lets have a look at the routing table
R3#sh ip route 140.0.0.0
Routing entry for 140.0.0.0/24, 1 known subnets
B 140.0.0.0 [200/0] via 4.4.4.4, 00:03:16
It is present in Routing table also
Now lets check on R1
R1#sh ip route 140.0.0.0
Routing entry for 140.0.0.0/24, 1 known subnets
B 140.0.0.0 [20/0] via 13.1.1.3, 00:04:34 ------------> Getting learned via R3
It is present in Routing table of R1 also
That means BGP Synchronization is disable by default
Now lets enable BGP Synchronization on R3
R3#sh run | section bgp
router bgp 300
bgp log-neighbor-changes
network 30.1.1.0 mask 255.255.255.0
network 30.1.2.0 mask 255.255.255.0
network 30.1.3.0 mask 255.255.255.0
network 30.1.4.0 mask 255.255.255.0
neighbor 4.4.4.4 remote-as 300
neighbor 4.4.4.4 description **iBGP with R4**
neighbor 4.4.4.4 update-source Loopback0
neighbor 13.1.1.1 remote-as 100
neighbor 13.1.1.1 description **eBP with R1**
R3(config)#router bgp 300
R3(config-router)#synchronization
R3(config-router)#^Z
R3#
R3#sh run | section bgp
router bgp 300
synchronization ==================================> enabled
bgp log-neighbor-changes
network 30.1.1.0 mask 255.255.255.0
network 30.1.2.0 mask 255.255.255.0
network 30.1.3.0 mask 255.255.255.0
network 30.1.4.0 mask 255.255.255.0
neighbor 4.4.4.4 remote-as 300
neighbor 4.4.4.4 description **iBGP with R4**
neighbor 4.4.4.4 update-source Loopback0
neighbor 13.1.1.1 remote-as 100
neighbor 13.1.1.1 description **eBP with R1**
R3#clear ip bgp * soft in
R3#clear ip bgp * soft out
R3#sh ip route 140.0.0.0
% Network not in table
R3#
R3#sh ip bgp 140.0.0.0
BGP routing table entry for 140.0.0.0/24, version 0
Paths: (1 available, no best path)
Not advertised to any peer
Refresh Epoch 2
Local
4.4.4.4 (inaccessible) from 4.4.4.4 (40.1.4.1)
Origin IGP, metric 0, localpref 100, valid, internal, not synchronized
rx pathid: 0, tx pathid: 0
Now you can see the route is present in BGP but not in the routing table
Lets check on R1
R1#sh ip route 140.0.0.0
Routing entry for 140.0.0.0/24, 1 known subnets
B 140.0.0.0 [20/0] via 2.2.2.2, 00:03:51 =========> it is stop learning via R3 and now its learning via R2
Thanks for Reading !!!!!
amartechstuff