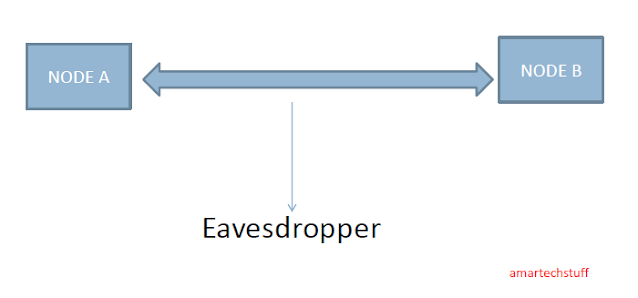
Eavesdropper
The attacker who listens to communication between nodes (Here Node A & Node B)
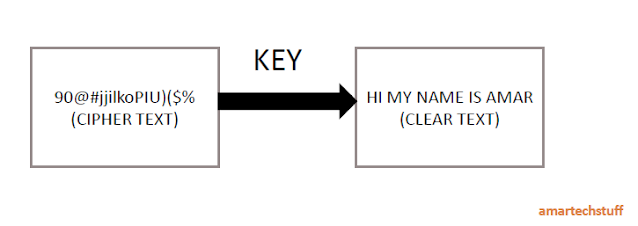
Encryption
Encryption is a process of converting clear text into cipher text which help of key and encryption algorithm.
Decryption
Decryption is a process of converting cipher text into clear text which help of key and encryption algorithm.
Types of Encryption
•Symmetric Encryption
•Asymmetric Encryption
Symmetric Encryption
•In Symmetric Encryption same key is used for Encryption and Decryption.
•Problem with exchange of key .
•Process is fast.
•Cipher Text size is less.
Asymmetric Encryption
•Asymmetric Encryption different keys are used for Encryption and Decryption.
•Public Key-Encryption is done.
•Private Key- Decryption is done.
•No Problem with Exchange of key.
•Cipher Text is large
•More Secure .
Symmetric Encryption Algorithms
•Data Encryption Standard (DES)
-Uses single 56 bits key.
- Weak Security .
-Uses single 56 bits key.
- Weak Security .
•3 Data Encryption Standard (3DES)
- Uses three 64 bits keys.
- Moderate Security.
- Uses three 64 bits keys.
- Moderate Security.
•Advanced Encryption Standard (AES)
• -Uses Rijndael Alogrithm.
• - Capable of using 128 bits , 192 bits and 256 bits keys.
• - Most Secure Symmetric Encryption Algorithm.
• -Uses Rijndael Alogrithm.
• - Capable of using 128 bits , 192 bits and 256 bits keys.
• - Most Secure Symmetric Encryption Algorithm.
Asymmetric Encryption Algorithms
Rivesh Shamir Adlemen (RSA)
-Was Released in 1978 by Ron Rivest , Adi Shamir & Len Adlemen
-Includes 4 Operational Steps
> Key Generation
> Key Distribution
> Encryption
> Decryption
> Key Distribution
> Encryption
> Decryption
Thanks for Reading
amartechstuff

very useful and informative.
ReplyDeletethanks for reading
DeleteSir thank you very much for share this knowledge over here its very helpful for me.
ReplyDelete